Top of Page
- Links to move inside this page.
IIJ Firewall Management Service
Service Menu
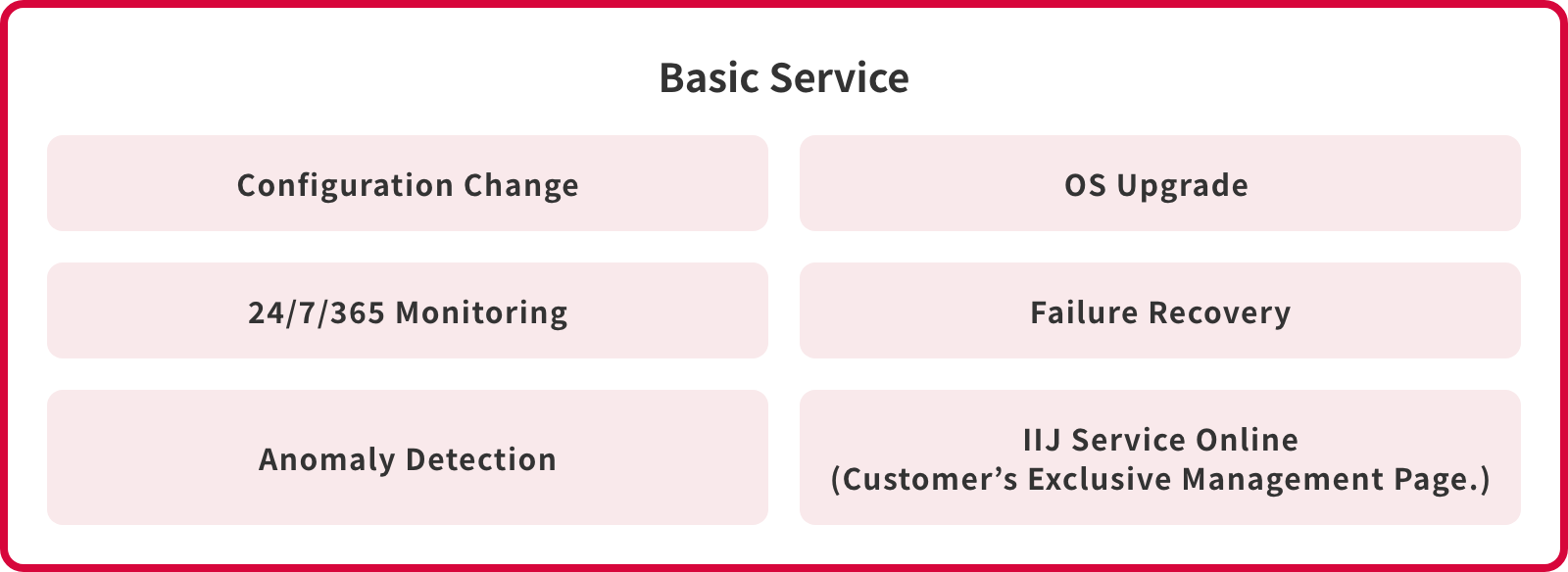
Basic services
* About the availability of firewall devices
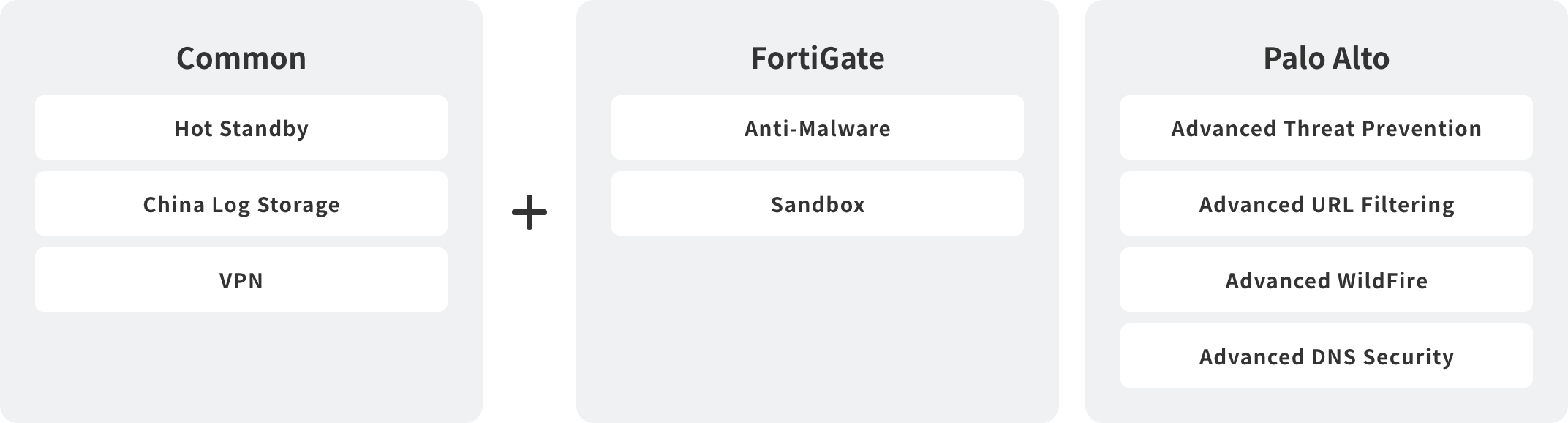
- You can choose from the FortiGate series and FortiGate VM series by Fortinet, Inc., or the PA series and Palo Alto VM series by Palo Alto Networks.
- The customer can supply the devices themselves or have them provided by IIJ.
Optional services
Main Features Provided (Basic Services)
| Proxy for configuration change tasks | We perform configuration changes on firewall devices on your behalf when needed. If you have any concerns about security risks, we will propose alternative configurations. |
|---|---|
| Proxy for OS upgrades and patch applications | We perform OS upgrades and patch applications on your behalf when needed. The functionality of each operating system and patch is confirmed by our company in advance. |
| 24/7 operational status monitoring | The IIJ monitoring host monitors the operational status of customer firewall devices 24/7. |
| Notification of failures and recovery operations | Upon detecting a connection drop or abnormal device behavior, we immediately contact the registered representative to report incidents and perform recovery operations. |
| Abnormality detection using IIJ's proprietary anomaly detection system | This system analyzes firewall communication logs and learns the unique communication patterns of each customer. It detects abnormalities when irregular communication patterns that deviate from the norm occur. |
| Monthly English report provision | We provide monthly PDF reports that summarize the statistics collected through one month of log analysis results. |
Contributing to the Resolution of Many Customers' Issues
- We have numerous overseas offices worldwide, but the Japanese Headquarters was unable to grasp the current IT situation at each location. Therefore, we implemented the IIJ Firewall Management Service (IFMS) across all locations, leading to the application of a unified security policy and strengthening our governance.
- One of our foreign subsidiaries experienced unauthorized access, resulting in a leak of personal information, including customer data. By implementing the IIJ Firewall Management Service, we were able to reassess the security operations previously managed by our foreign subsidiaries and enhance our security.
- We acquired a local company through an M&A, but due to the absence of dedicated IT staff, the firewall was operated with minimal configuration. By implementing the IIJ Firewall Management Service, we were able to outsource the operation and maintain optimal configuration, even without the relevant staff present.
Frequently Asked Questions
Q. Is the firewall equipment provided by IIJ?
The firewall equipment is not included with this service, but we can offer it separately upon request.
Q. What are the advantages of using IIJ's service compared to other providers?
Using IIJ's proprietary system enables quick detection of irregular communication. In addition to high-level support backed by years of expertise, our security engineers at overseas sites offer assistance in multiple languages.
Q. Is the service available in every country?
We already provide this service in various countries. Please contact us for details on the countries and regions where it is available.
- Related Contents
End of the page.